【人気ダウンロード!】 Secure Web Zones Inc 155685-Secure Web Zones Inc
ZoneAlarm Web Secure Free is an advanced Chrome extension that provides you with essential browsing security tools to keep you safe from various threats while you search and browse the web Web Secure Free protects you from Phishing attempts, prevents you from downloading malicious documents and alerts you about potentially harmful websitesZones is an authorized tierone hardware and software solutions partner with leading IT manufacturers such as IBM, HP, Lenovo, Apple, Cisco, Dell, EMC, Microsoft, Adobe, Oracle, Symantec and VMware In all, the Zones portfolio represents more than 2,000 suppliers in the support of our clients' unique IT infrastructure and business modelCyber Security Bluezone Secure IT offers Sophos cyber security products and services to smaller companies who are seeking an enterprise quality solution This includes every level of defense from personnel training and assessment to network firewall protection with intruder detection and response capability Learn more Training

Security For Your Company Jablotron
Secure web zones inc
Secure web zones inc-Zones Profile and History Zones is a global IT solutions provider headquartered in Auburn, Washington They offer workplace modernization, network optimization, data center transformation, and security fortification services for businesses around the world The company was founded inSecure Web Zones, Inc Makati City, Makati, Philippines 101 499 BPO Overview Jobs (0) Company Description The company has a formal license, is a fastgrowing, innovative technology and lead the application of network technology company
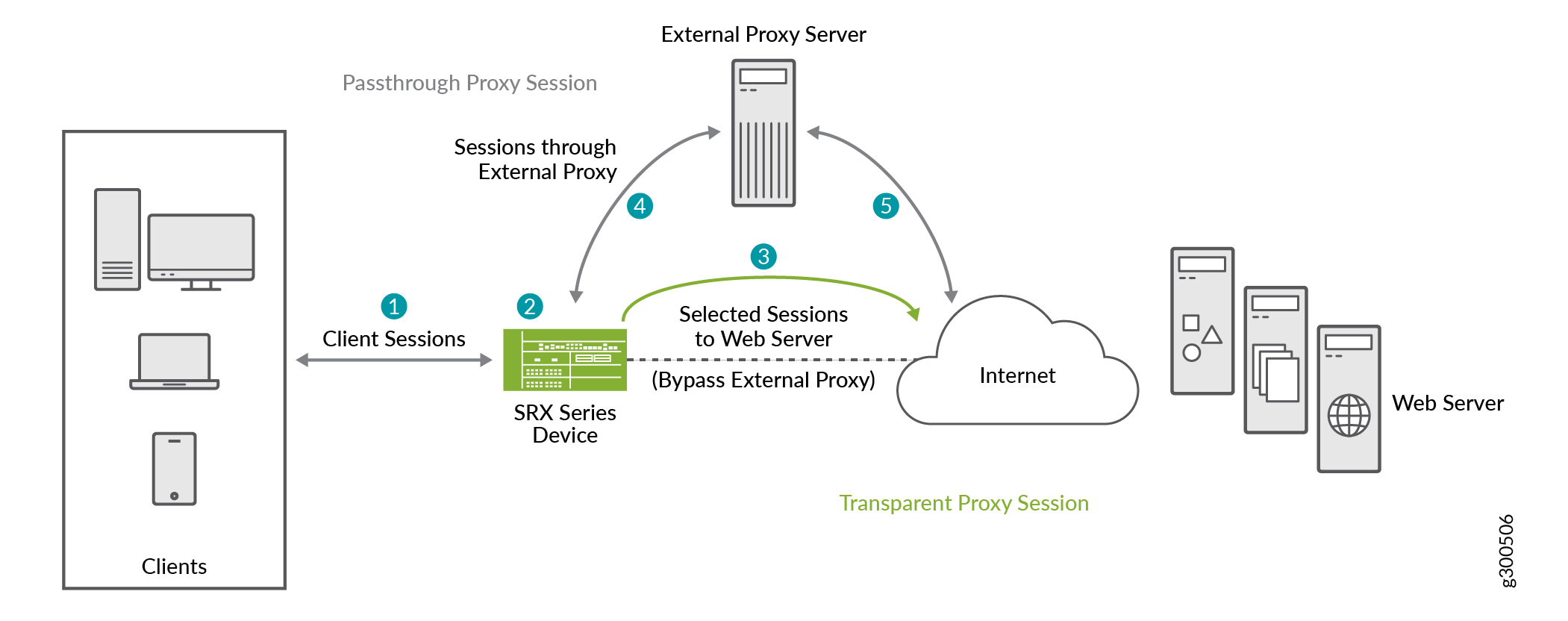



Secure Web Proxy Junos Os Juniper Networks
Web Zone IT Services provides internet marketing services that includes onsite optimization, content strategy and building and developing authority of the website within related business industry by following the best practices and guidelines of search engine We have a skilled and experienced team of search engine marketers to deliver greatSecure Zone based in Lisburn, provides quality assured products & services throughout Northern Ireland Our Experience & Expertise guarantees an Excellent level of service, protecting your Home & Business premises against Fire, Theft & Vandalism Securing your World, isApply to Secure Web Zones jobs available on Indeedcom, the worlds largest job site Secure Web Zones Work, Jobs 14 March, 22 Indeedcom Philippines Skip to Job Postings , Search
About Us Zone Secure is founded on years of experience supplying crowd barrier systems and temporary fencing to large events, festivals, shows, sporting venues and exhibitions We now also supply permanent sport fencing as seen at all major sporting venues We are stockists of new and used fencing and barrier systems, ready to sell or hire outSIMPLE CORE VALUES Our values are simple work together, learn together – and serve our customers with integrity, commitment and passion By embracing this ethos, Zones can solve the immediate business challenges of the modern working environment – flexibility, productivity, scalability, compatibility, and security – and continue to innovate, adapt and growSecure Web Zone Nob 19 Kasalukuyan 1 taon 10 buwan Makati Supervising Visa of all expat Management Admin team, include but not limited to Dorm, Shuttle, Purchasing, Event Planning, Interpretation and Emmergency Assist Management company's all local employee and expat HR team, include but not limited to Recruitment, Staffing
SecurityZONES provides realtime threat intelligence data via antispam blocklists and IP/Domain Reputation Datafeeds that protect 3 billion email users from malware, phishing, and botnet threats every day Spamhaus Passive DNS SURBL Contact Us DNS Firewall (RPZ) Read our latest Security Blog Spamhaus 4Q Botnet Report (21)Zones act as secure containers, making it easy for users to clearly organise content within folders while keep sensitive content safe from unauthorised access Comprehensive user permissions Your people can set permissions for how peers and third parties interact with files, including restrictions on copying or editing, downloads, forwarding, location access, and time of accessSECURE WEB ZONES, INC (PAGCOR REGISTERED/BPO) INTERNAL COMPANY PROCESS Setup Company Books of Account into Google Sheet Upgrade Company Books of Account into QUICKBOOKS Accounting System



Smartrecruiters Security Overview Smartrecruiters
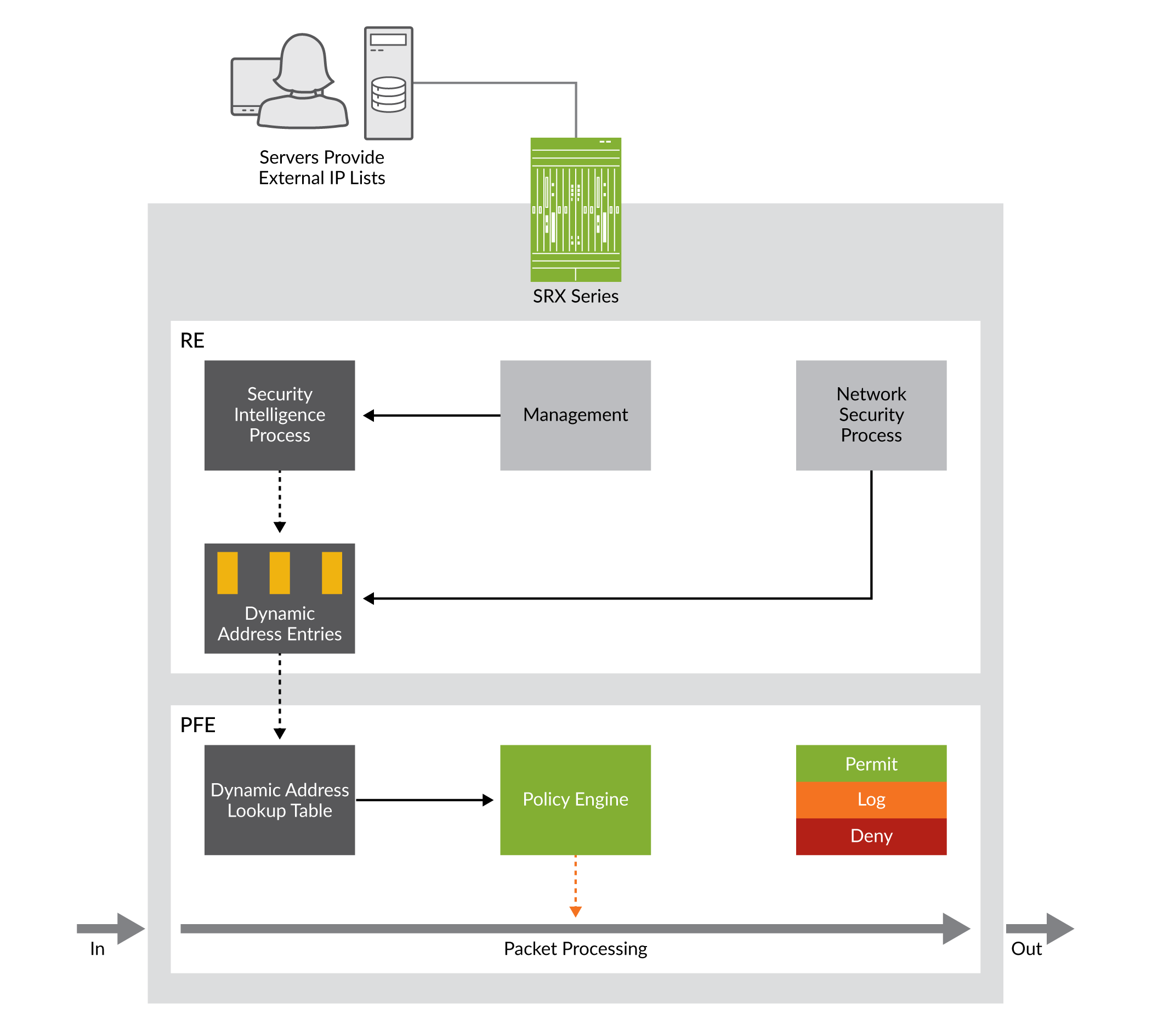



Configuring Security Policies Junos Os Juniper Networks
Internet Explorer and Legacy Edge use a system of five Zones and URLActions to make security decisions for web content, based on the host of a target site Chromium (New Edge, Chrome) uses a system of Site Lists and permission checks to make security decisions for web content, based on the hostname of a target siteThe WEBZONES company has been established in late 08 Currently it provides services mainly in the field of technical implementation of websitesZones Working Together Reflecting on how our clients think about solutions and how their IT and Procurement teams are organized, we have aligned our offerings to a more uniformed platform that addresses the immediate business challenges of today – flexibility, productivity, scalability, compatibility, and security




Creating A Multi Region Application With Aws Services Part 1 Compute Networking And Security Aws Architecture Blog
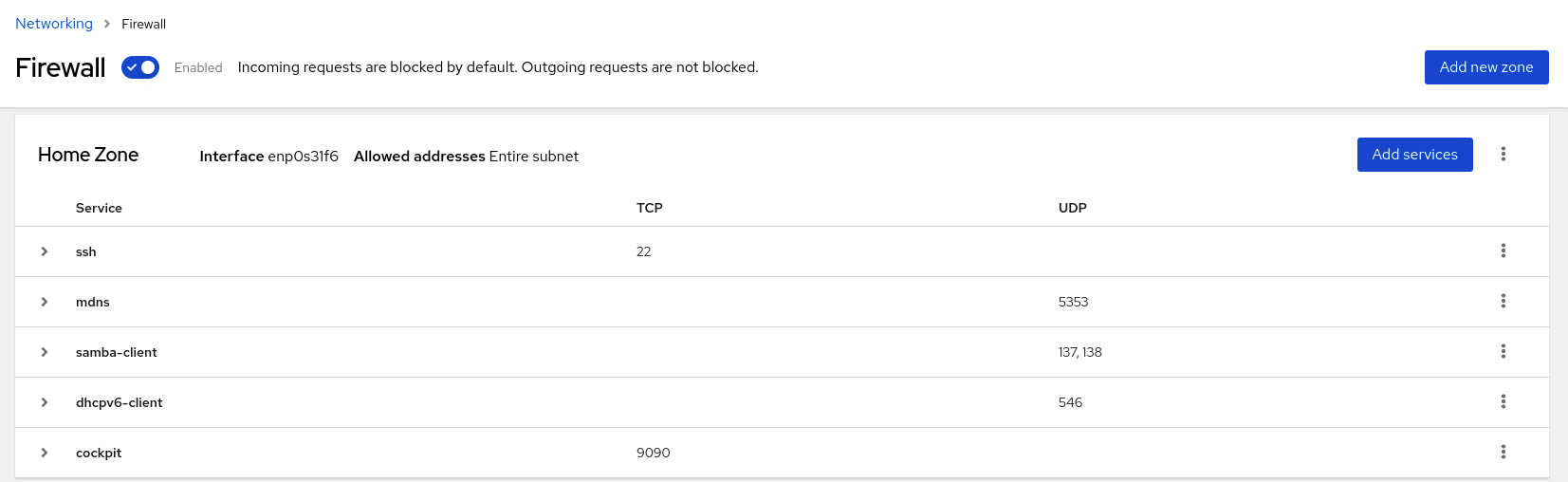



Managing Systems Using The Rhel 8 Web Console Red Hat Enterprise Linux 8 Red Hat Customer Portal
The main objectives of security zones are to protect the network, detect intruders, contain attacks, and prevent these interferences from reaching the internal network Even with security zones inA Holistic Approach to Defending Your IT Infrastructure Zones is your endtoend professional and managed services partner for vulnerability assessments, managed security operations, access policies and information security governance Cybercrime is a profitable business And business has been good The pandemicinduced shift to remote and hybrid work has made organizationsZones Our IT solutions address the business challenges of today – flexibility, productivity, scalability, compatibility, and security More information Workplace Modernisation With remote working now a reality, the best talent can be sourced from anywhere in the world A solid network will ensure consistent worker uptime and effective



How To Secure Web Applications With Aws Waf Edureka



Virtual Workforce And Work From Home Solutions Alorica
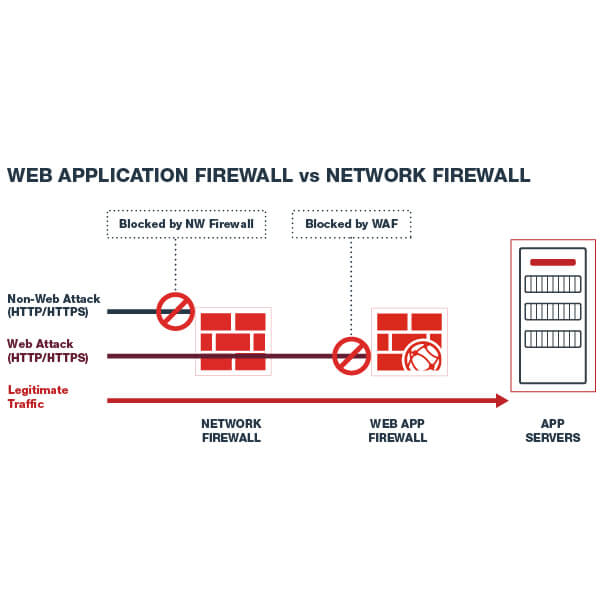



Waf Vs Firewall Web Application Network Firewalls Fortinet




How To Secure Web Applications With Aws Waf Edureka



2




Maximize Your Cloud Security With Isolation Zones Infoworld




Skylight Home



Zones Reviews 3 Reviews Of Zones Com Sitejabber




Building A Serverless Web Application Architecture For The Aws Secure Environment Accelerator Asea Aws Public Sector Blog
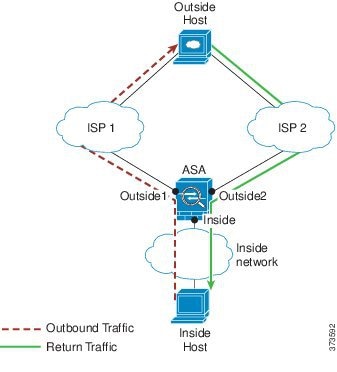



Cli Book 1 Cisco Asa Series General Operations Cli Configuration Guide 9 6 Traffic Zones Cisco Asa 5500 X Series Firewalls Cisco




Homepage Family Locator




Operating System Security Hardening Guide For Sap Hana For Suse Linux Enterprise Server 15 Ga And Sp1 Suse Linux Enterprise Server For Sap Applications 15 Ga And Sp1




Nsx Gateway Firewall Elastic Layer 7 Firewall Vmware




Resources Archive Hillstone Networks




Protectlives Com Is For Sale




Integrating Aws Outposts With Existing Security Zones Aws Compute Blog
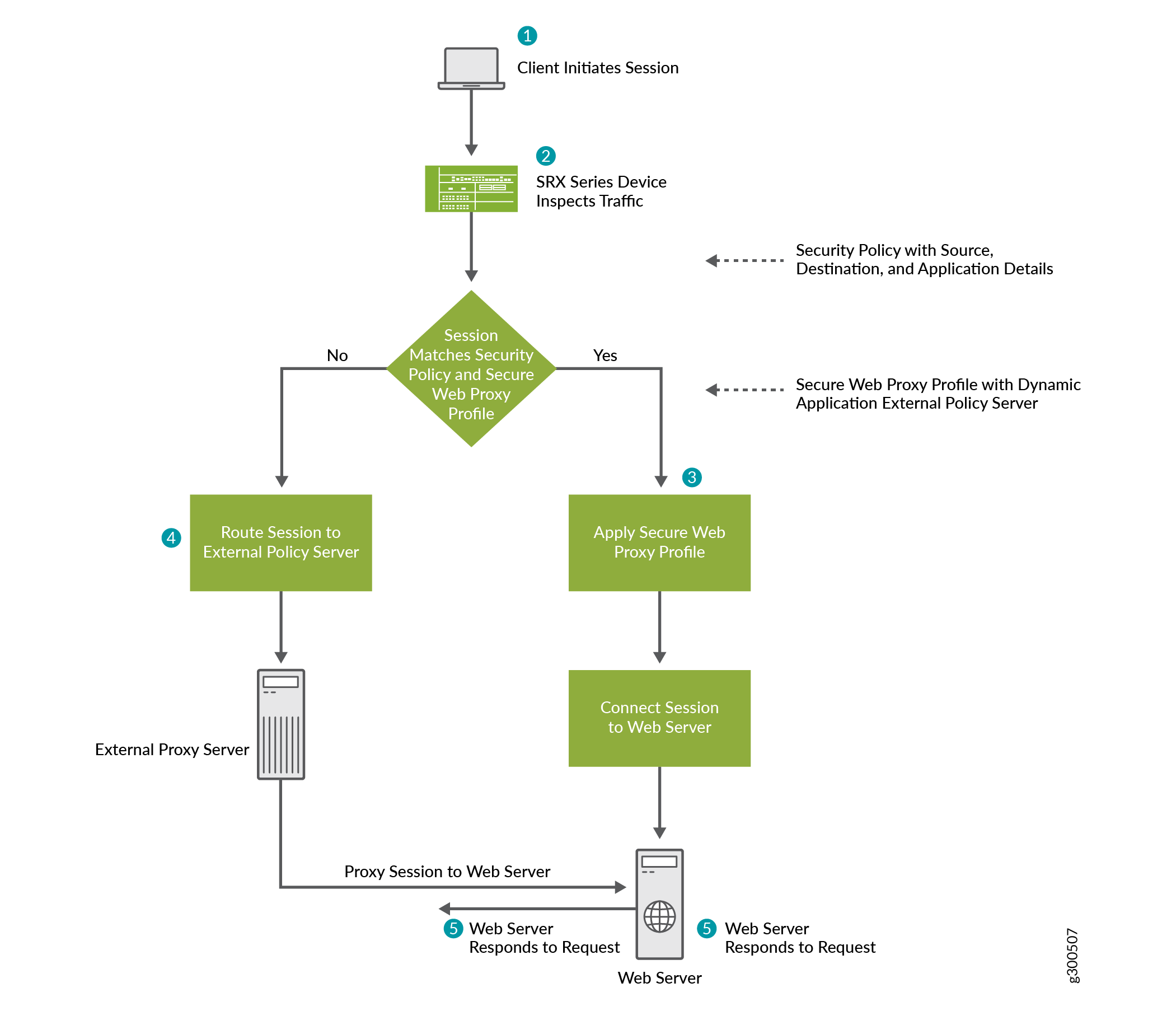



Secure Web Proxy Junos Os Juniper Networks




Best Practices For Securing Sensitive Data In Aws Data Stores Aws Database Blog




Zones Uk Ltd Linkedin
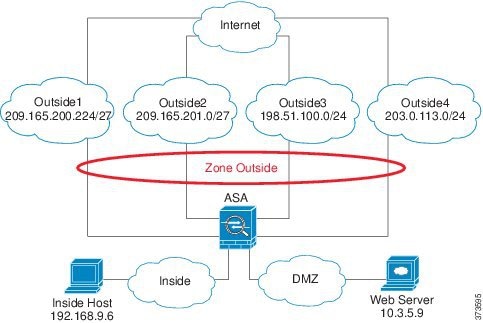



Cli Book 1 Cisco Asa Series General Operations Cli Configuration Guide 9 6 Traffic Zones Cisco Asa 5500 X Series Firewalls Cisco




Security For Your Company Jablotron
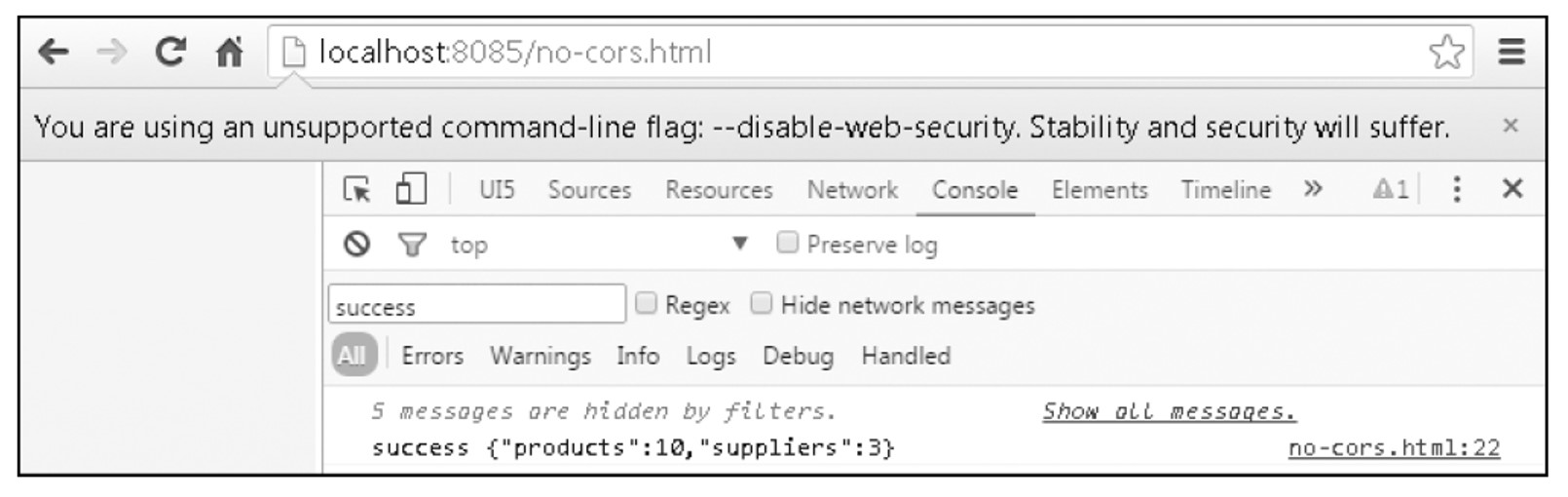



How To Disable Google Chrome Web Security For Sapui5
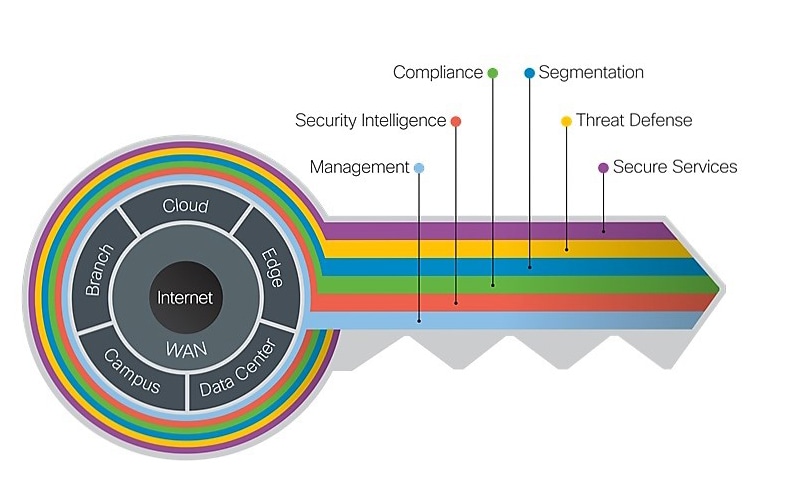



Design Zone For Security Safe Cisco



Authentic8 Com



Szdvqfhzylrmtm




Top 10 Zones Inc Alternatives 22 G2




Ppe Supplies Ltd Linkedin



2




How To Think About Zero Trust Architectures On Aws Aws Public Sector Blog




Launch Aws Faster Using Automated Landing Zones Aws Online Tech Tal



Waf For Everyone Protecting The Web From High Severity Vulnerabilities




Launch Aws Faster Using Automated Landing Zones Aws Online Tech Tal
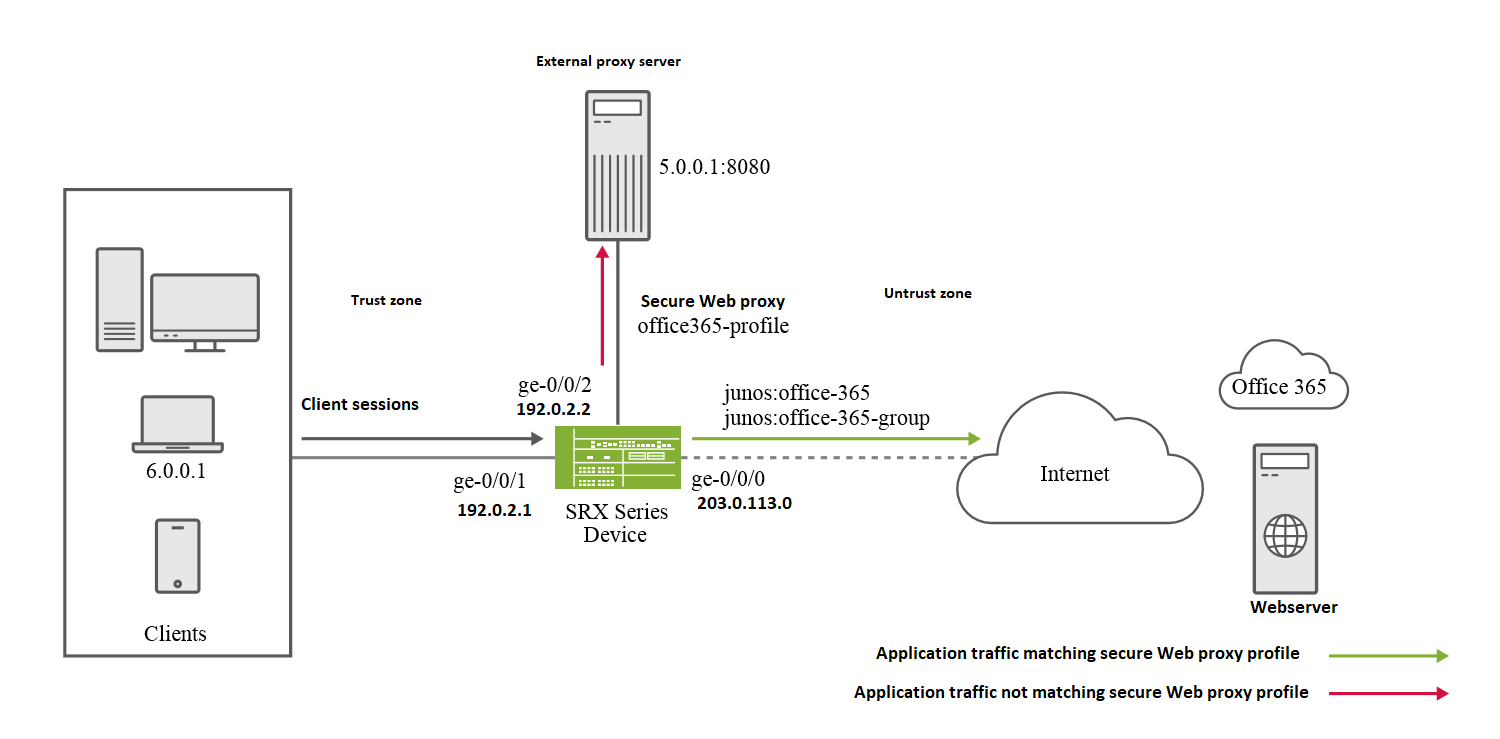



Secure Web Proxy Junos Os Juniper Networks




Top 10 Zones Inc Alternatives 22 G2




Resources Archive Hillstone Networks




Ozon About The Company



1




Secure Web Proxy Junos Os Juniper Networks




Ggxqy2nh9crcam




The Political And Security Dimensions Of The Humanitarian Health Response To Violent Conflict The Lancet




Zones Solutions Cybersecurity Solutions




What Are The Best Vpn Services For Conflict Zones Computerworld




World Free Zones Organization



Organic Maps Offline Hike Bike On The App Store
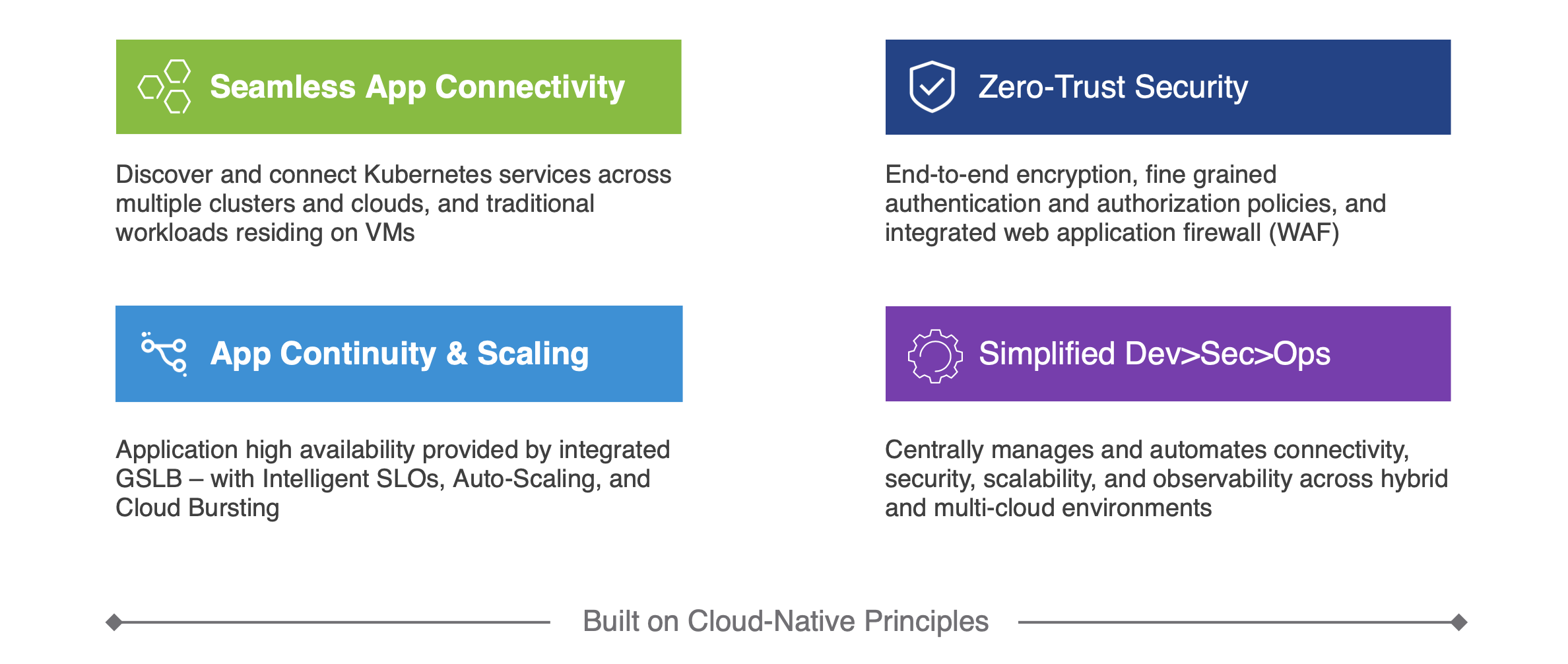



Multi Cloud Connectivity And Security Needs Of Kubernetes Applications
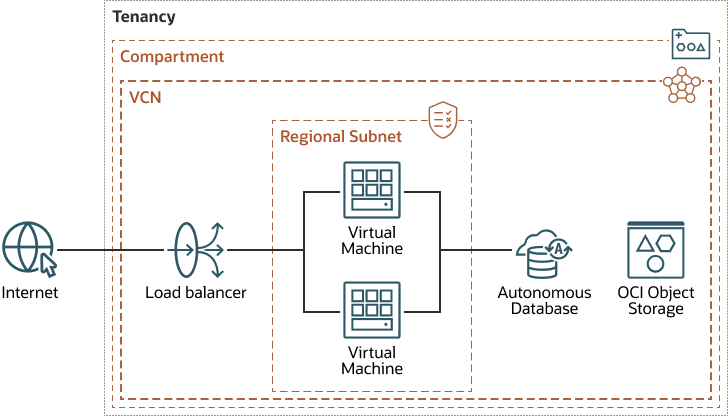



Protect Your Workloads In The Cloud Using Security Zones




Openshift And Network Security Zones Coexistence Approaches




Cloudflare The Web Performance Security Company Cloudflare



Cloudflare The Web Performance Security Company Cloudflare



1
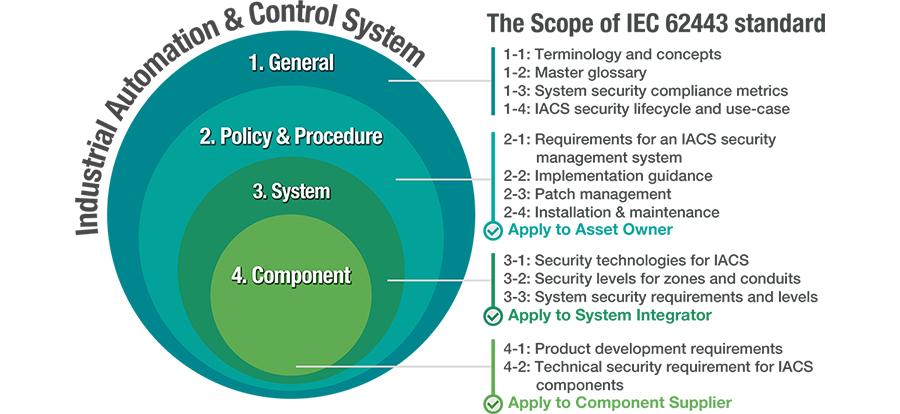



Enhance Industrial Network Security By Following The Iec 4 2 Standard




Aws Lambda Security Lumigo




Hardening The Security Of Your Aws Elastic Beanstalk Application The Well Architected Way Aws Security Blog
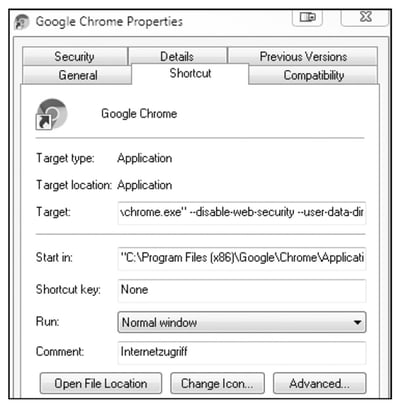



How To Disable Google Chrome Web Security For Sapui5
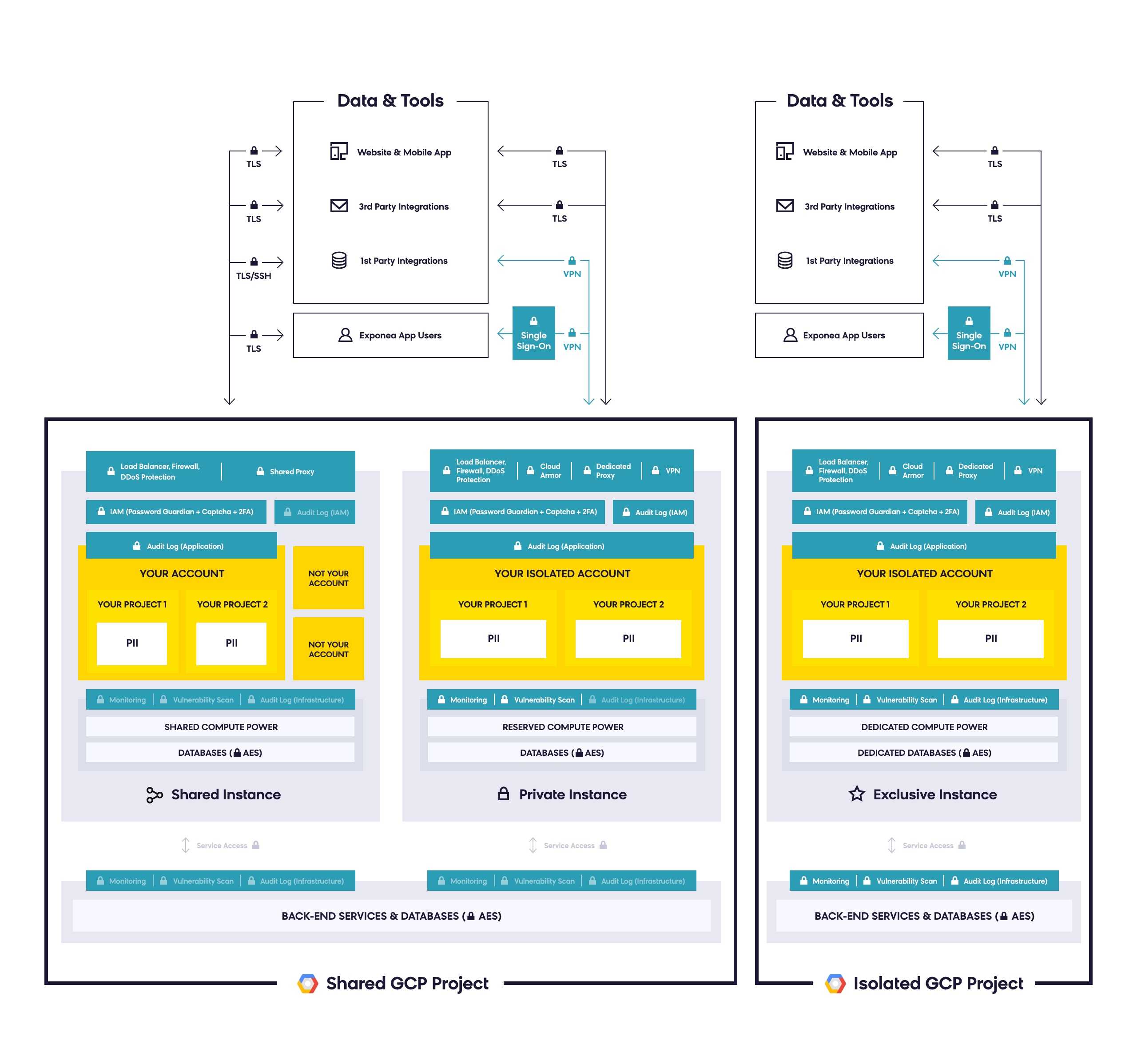



Security Architecture




Explainer The Very Bad History Of Safe Zones



2
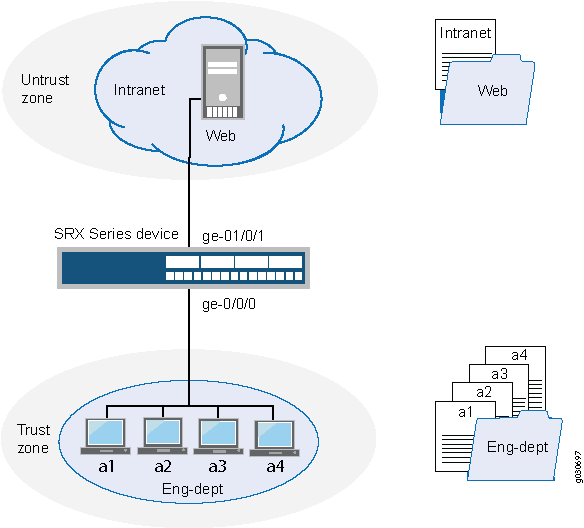



Address Books And Address Sets Junos Os Juniper Networks




Andrew Reese Practice Head Cyber Security Zones Llc Linkedin




Securing Industrial Networks What Is Isa Iec Cisco Blogs




Protectu Home Facebook




Openshift And Network Security Zones Coexistence Approaches




Ozon About The Company
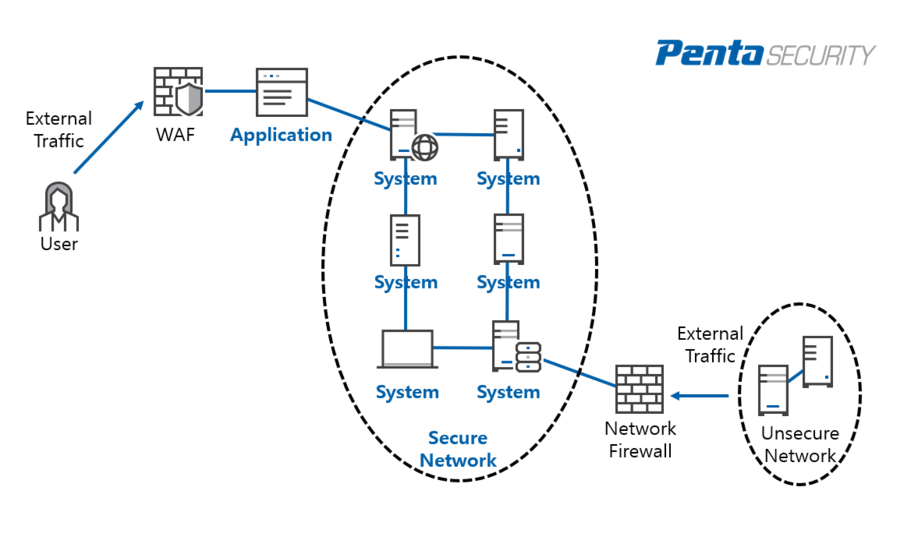



Why Do I Need A Web Application Firewall Penta Security Systems Inc
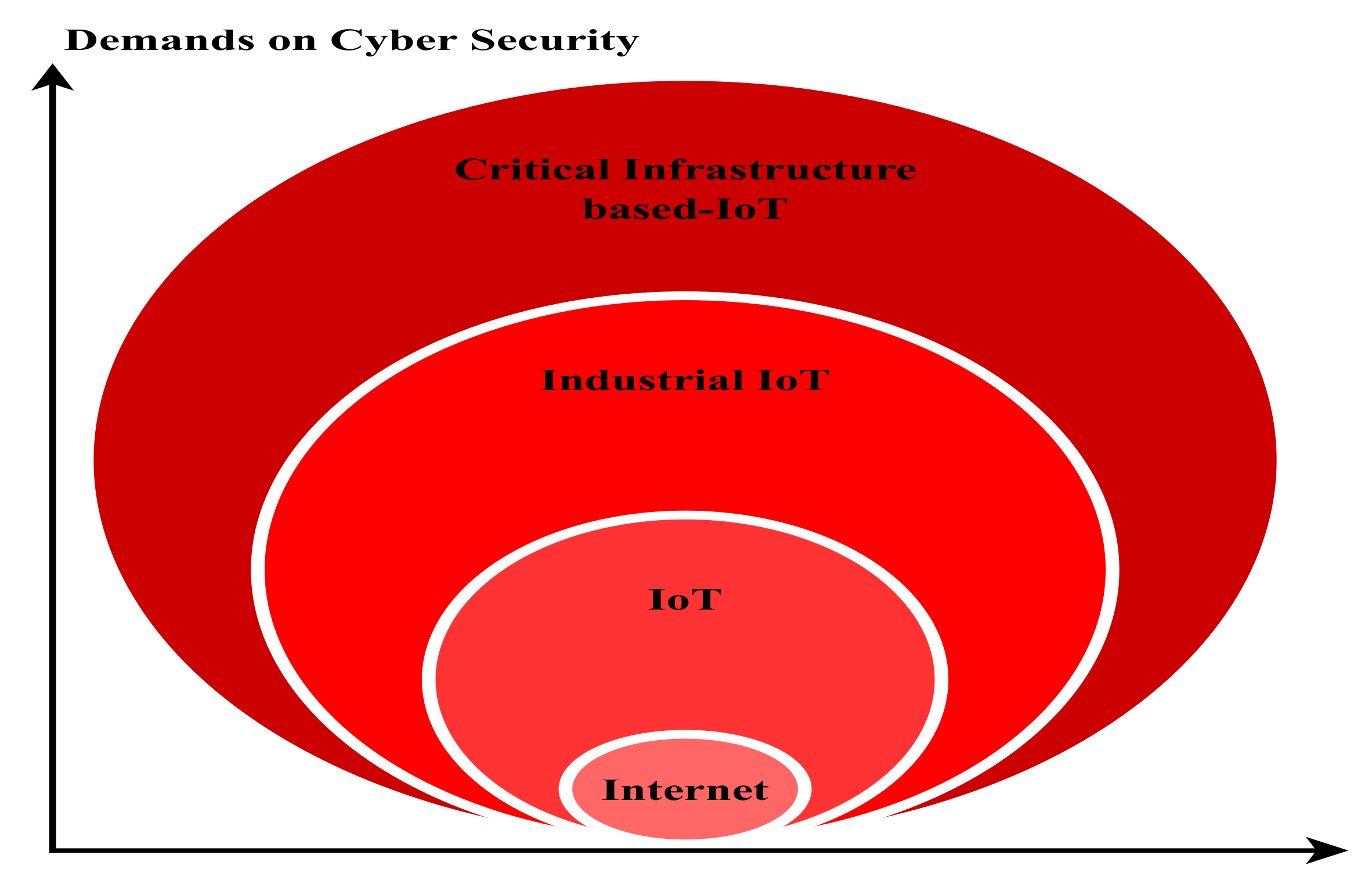



Applied Sciences Free Full Text Internet Of Things Meet Internet Of Threats New Concern Cyber Security Issues Of Critical Cyber Infrastructure Html




Openshift And Network Security Zones Coexistence Approaches




Working At Secure Web Zones Inc Bossjob
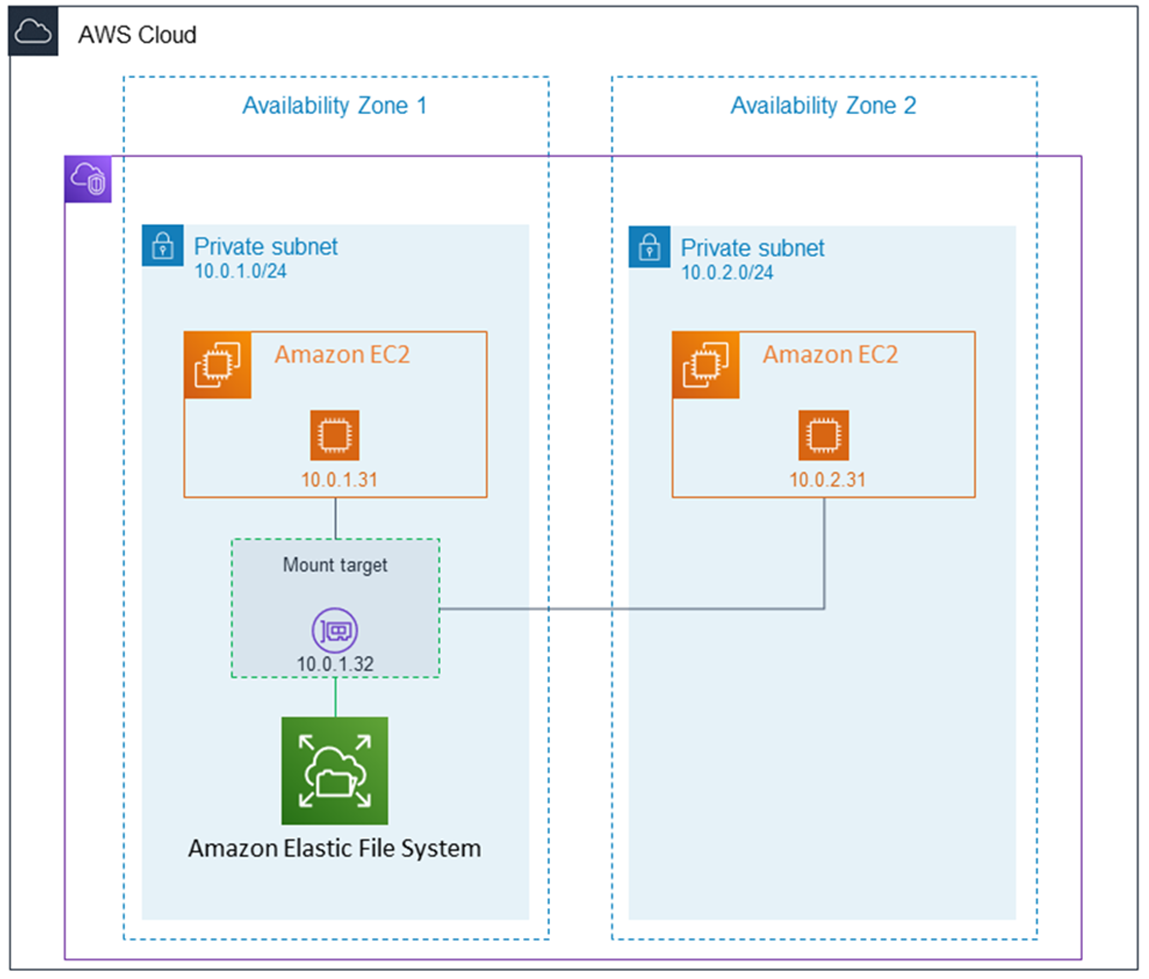



Creating And Managing Mount Targets And Security Groups Amazon Elastic File System



Pressreader
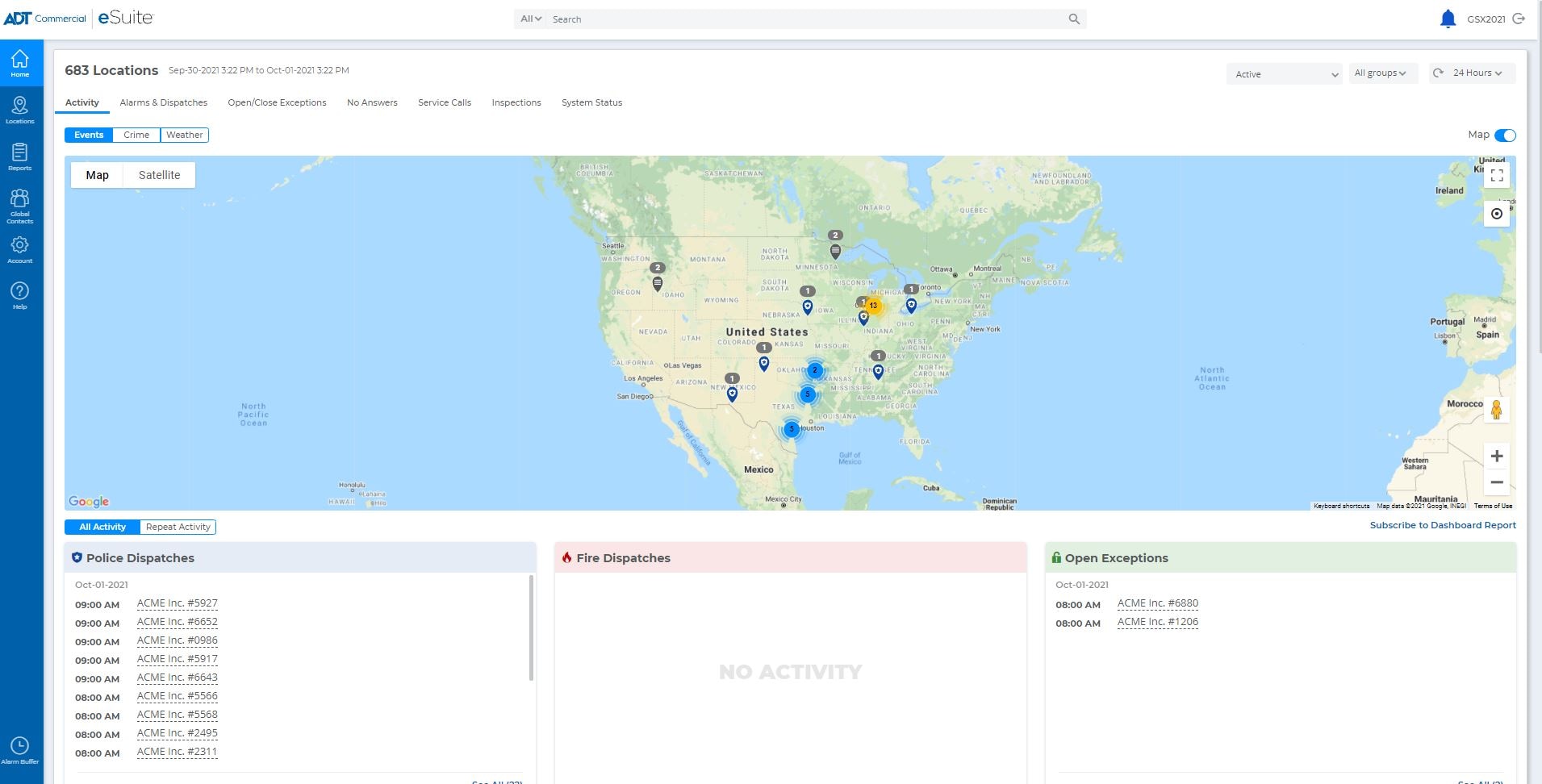



Esuite Security Account Management Adt Commercial




Your Trusted Travel Agent In Siem Reap Cambodia Icare Tours



2




Tech Brief Citrix Secure Internet Access Citrix Tech Zone




Face Body Vehicle And License Plate Number Recognition Ntechlab




Secure Web Zones Inc Jobs In Philippines
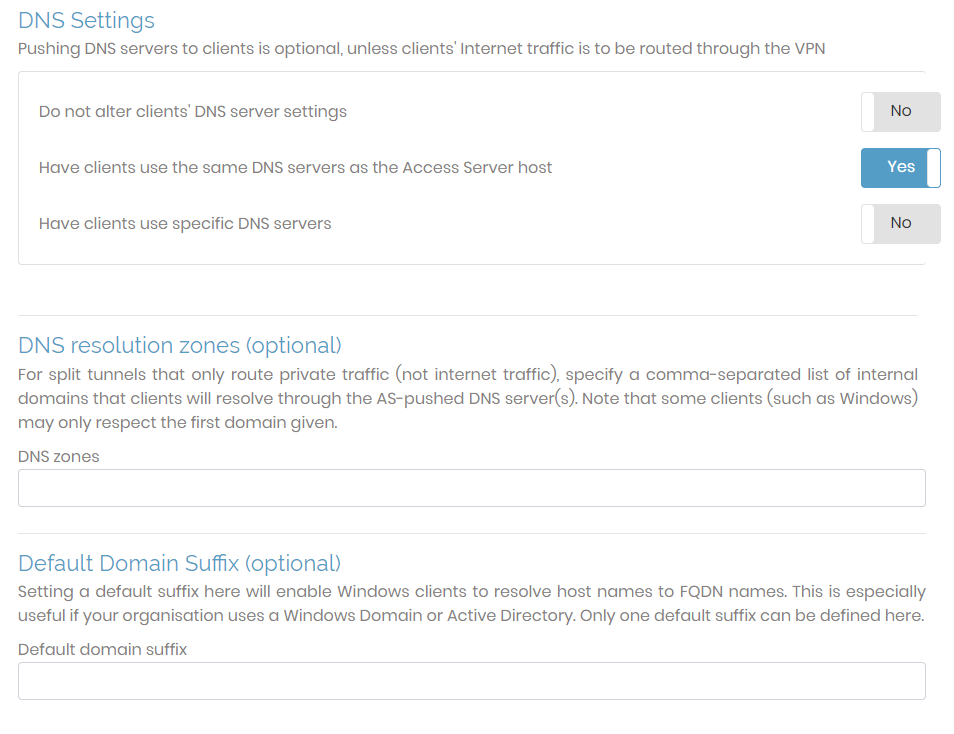



Vpn Settings Access Server Admin Guide Openvpn




What Is Aws Overview Services And Pricing Calculator Spiceworks Tech
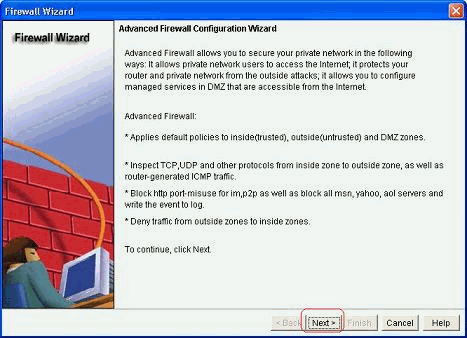



Cisco Cp Configure Zfw To Block Peer To Peer Traffic Cisco




Zones First Choice For It



1




Sonicwall Showcase




Shadow Iot How To Protect Your Organization Zscaler Blog




Working At Secure Web Zones Inc Bossjob
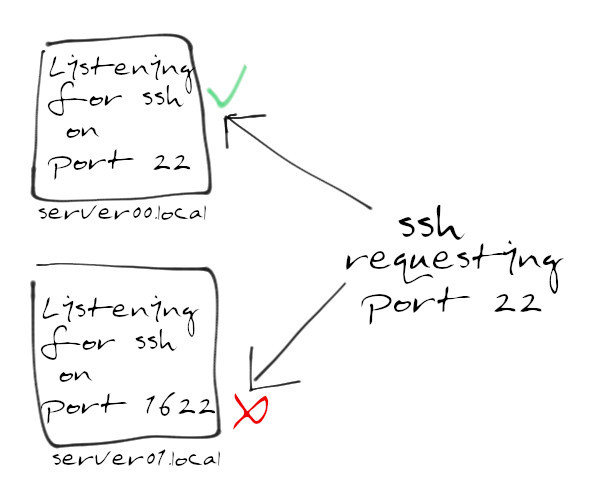



Secure Your Linux Network With Firewall Cmd Enable Sysadmin




Ultradns Firewall A Cloud Based Recursive Dns Neustar




Maximize Your Cloud Security With Isolation Zones Infoworld
コメント
コメントを投稿